All in all, it took a page from the OnePlus book that he himself authored and it seems to have paid off quite well. If we shift our attention towards custom development, then it seems to have performed quite decently in that segment as well. Its kernel source and device tree were released just days after the device launch. So custom ROMs and recovery might already be on their way. In the meantime, you could gain administrative access by rooting your device via Magisk. This in turn will allow you to welcome a plentitude of tweaks onto your device. However, this is just one side of the coun. As soon as you root the device, it will end up tripping the SafetyNet flag. As a result of which, banking and payment apps and games like Pokemon Go will no longer function. But fret not. Using a nifty workaround [changing Evaluation Type from Hardware_Backed to Basic] you could easily pass the Safetynet on your rooted Nothing Phone 1. And in this guide, we will show you how to do just that. Follow along.
How to Pass SafetyNet in Rooted Nothing Phone 1
Given below are two different methods to get this job done. The first method is the old and lengthier approach but initially, it was our only escape route. However, now there is a new and shorter approach available as well, which we have listed in Method 2 [recommended]. Both these methods should work across numerous Android devices [including the Nothing Phone 1]. Likewise, it should work on both Android 12 and 13 [should also work on older Android versions, but I haven’t tested them myself]. So on that note, let’s get started. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
METHOD 1: Pass SafetyNet using Magisk Hide Props Config [OLD]
This is the lengthier of the two methods and involves spoofing the device’s fingerprint to one of the older devices that followed Basic Attestation and were easier to bypass.
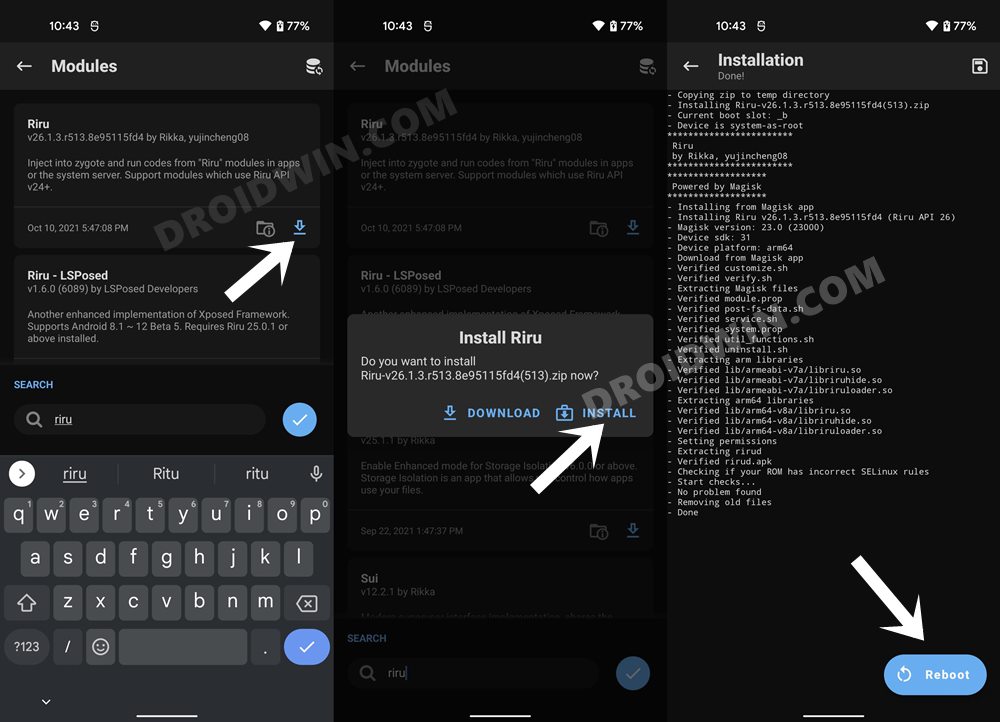
STEP 1: Install Riru Module on Nothing Phone 1
First off, you will have to install the Riru Module, which is a prerequisite for the SafetyNet Fix Module.
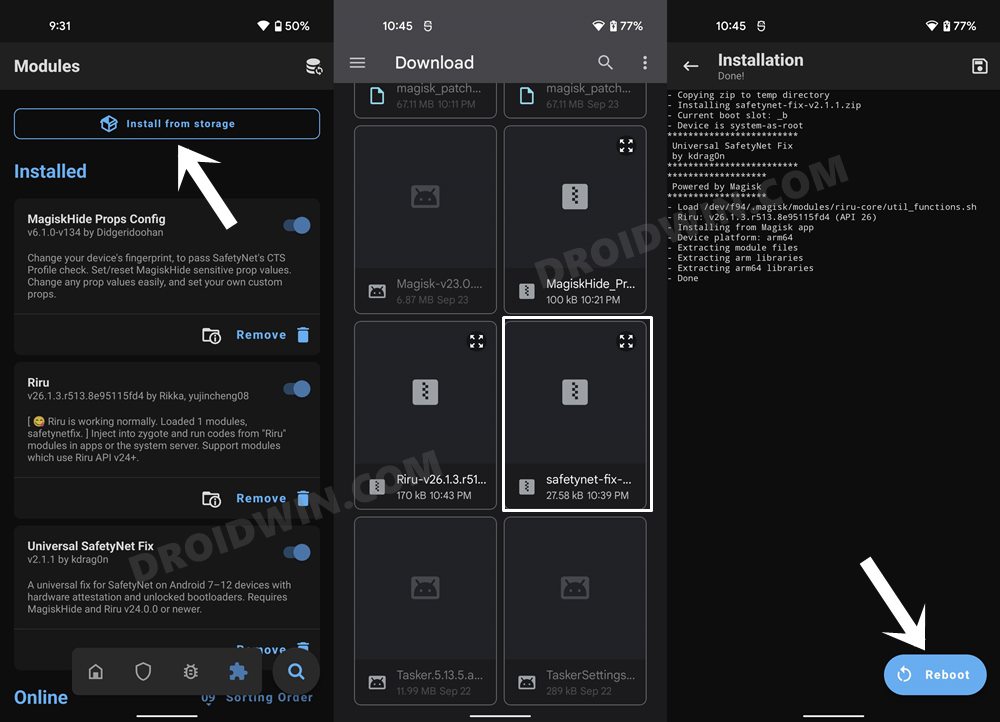
STEP 2: Flash Universal SafetyNet Fix on Nothing Phone 1
Next up, you will have to flash the latest version of the USNF (Universal SafetyNet Fix) module via Magisk. So refer to the below steps to try it out:
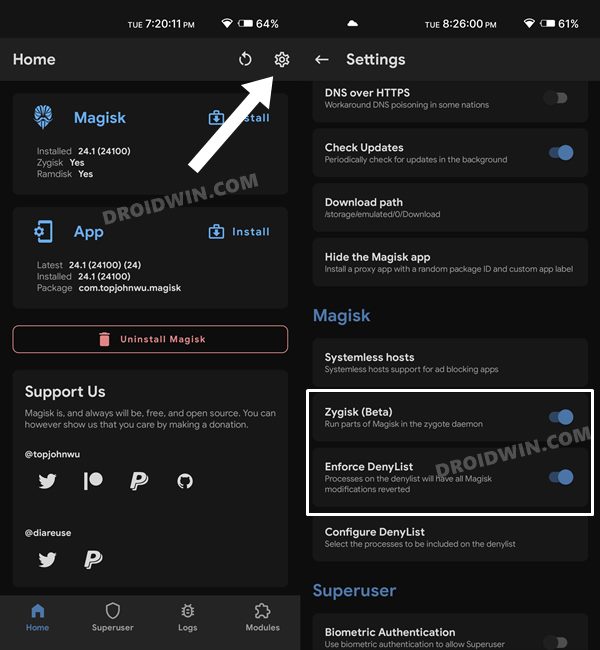
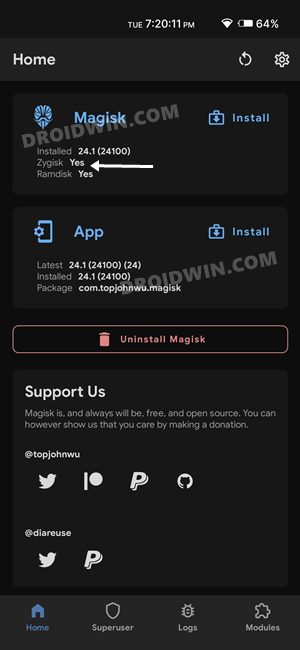
STEP 3: Enforce Deny List and Enable Zygisk on Nothing Phone 1
Deny List is the new name for Magisk Hide. For the unaware, it is the feature through which you could hide root from various installed apps onto your device. So let’s first enable this Deny List and then configure it according to the requirement.
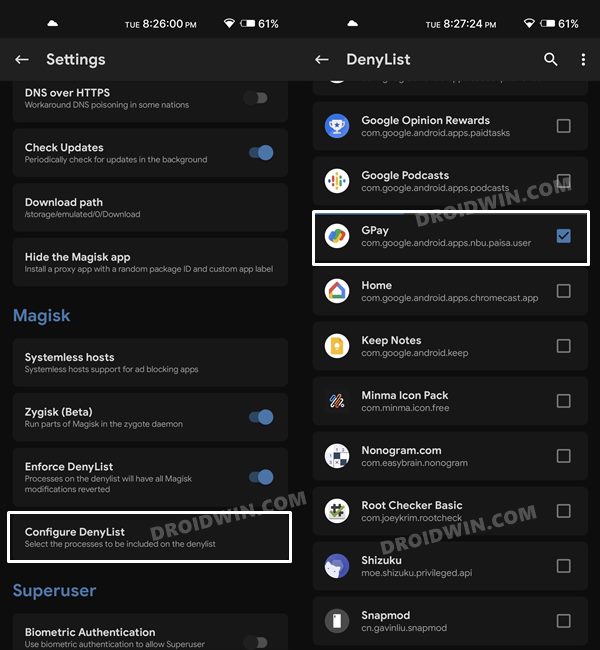
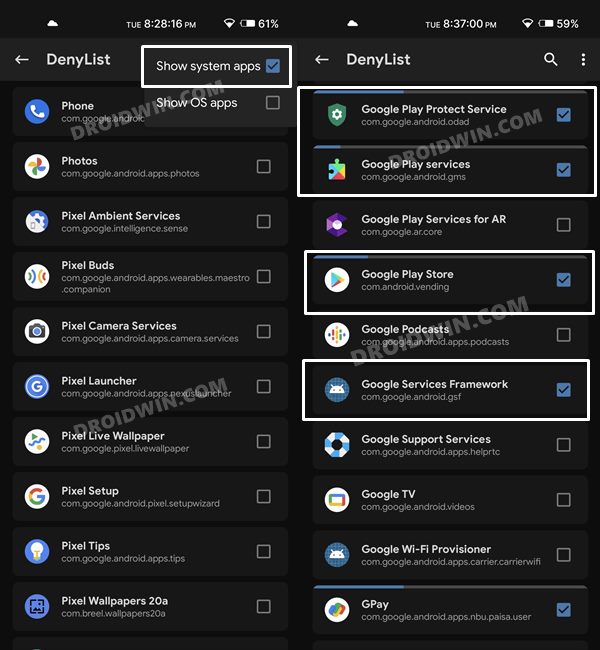
STEP 4: Configure Deny List on Nothing Phone 1
Deny List is the new name for Magisk Hide. For the unaware, it is the feature through which you could hide root from various installed apps onto your device. So let’s first enable this Deny List and then configure it according to the requirement.
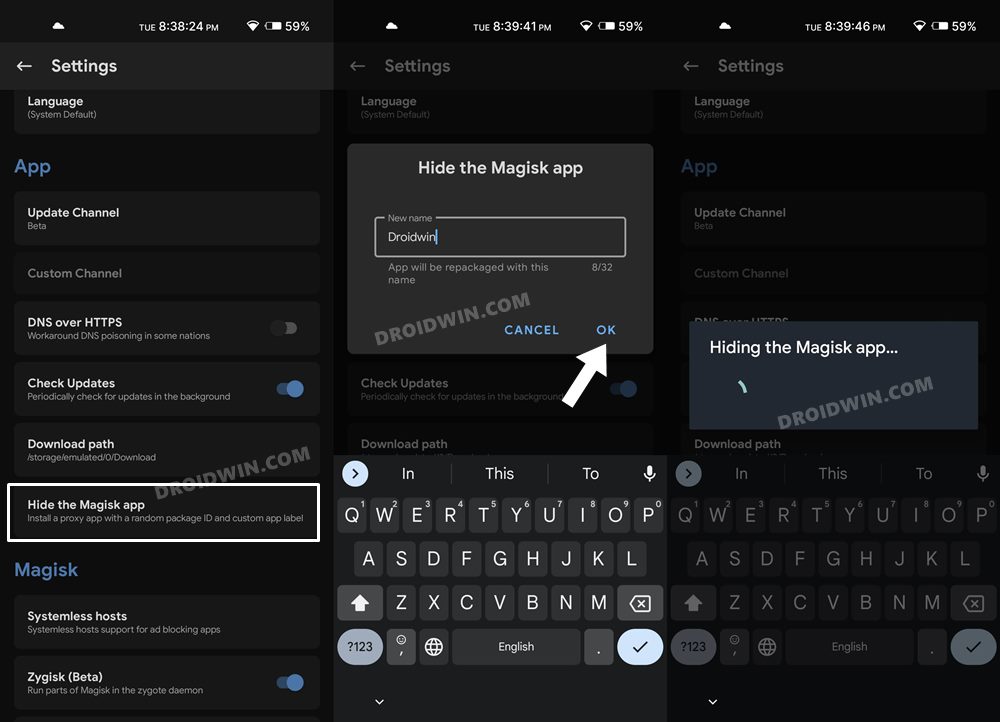
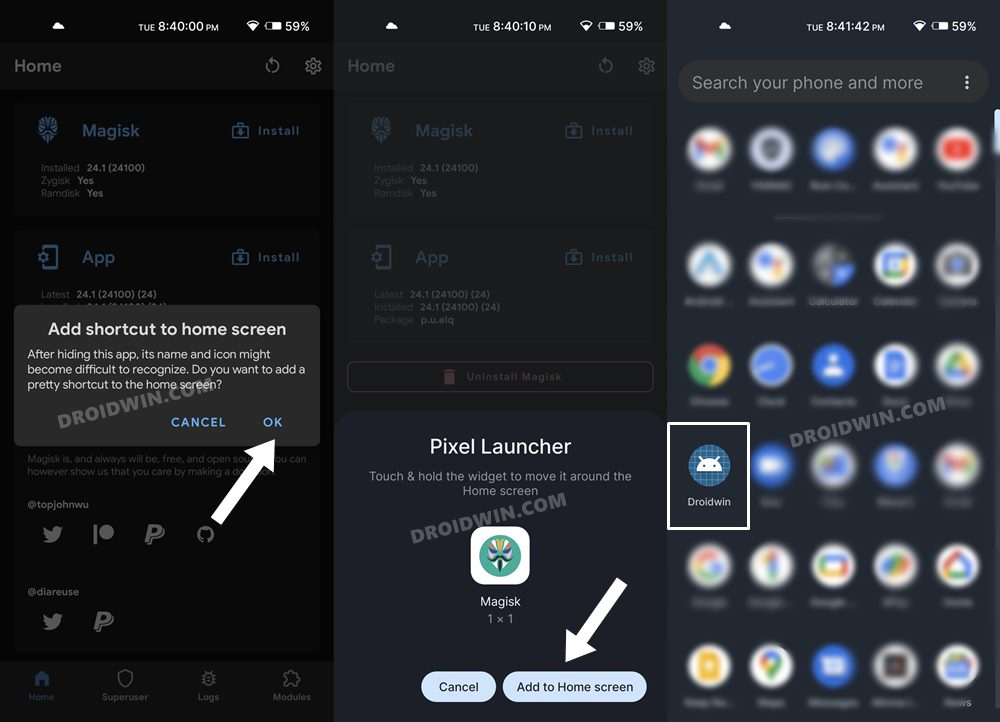
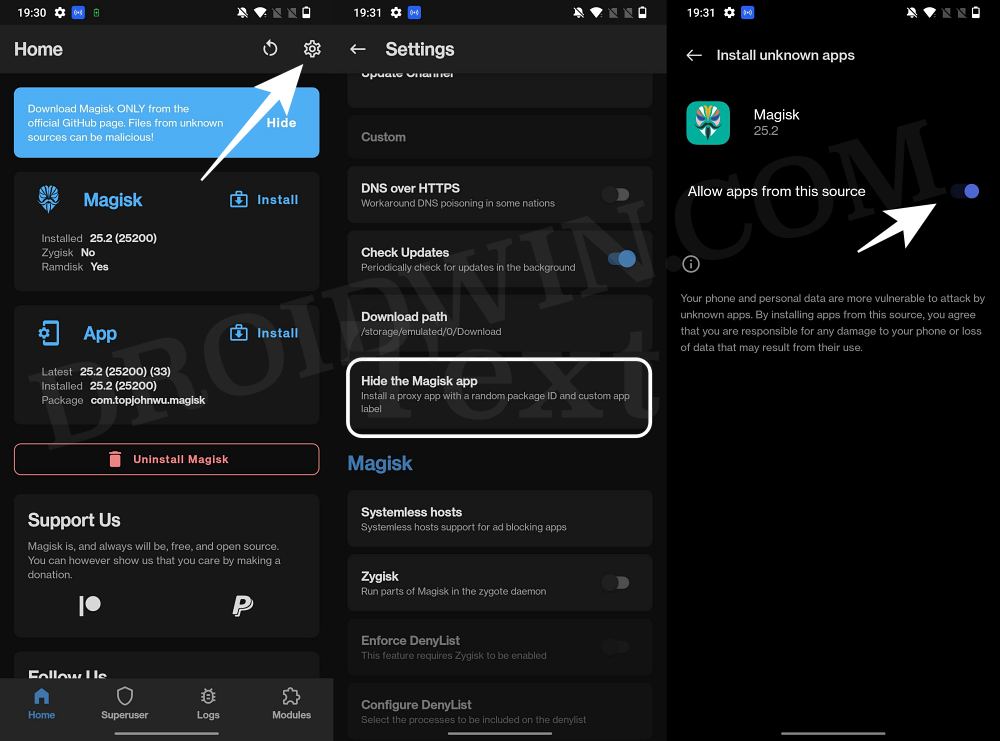
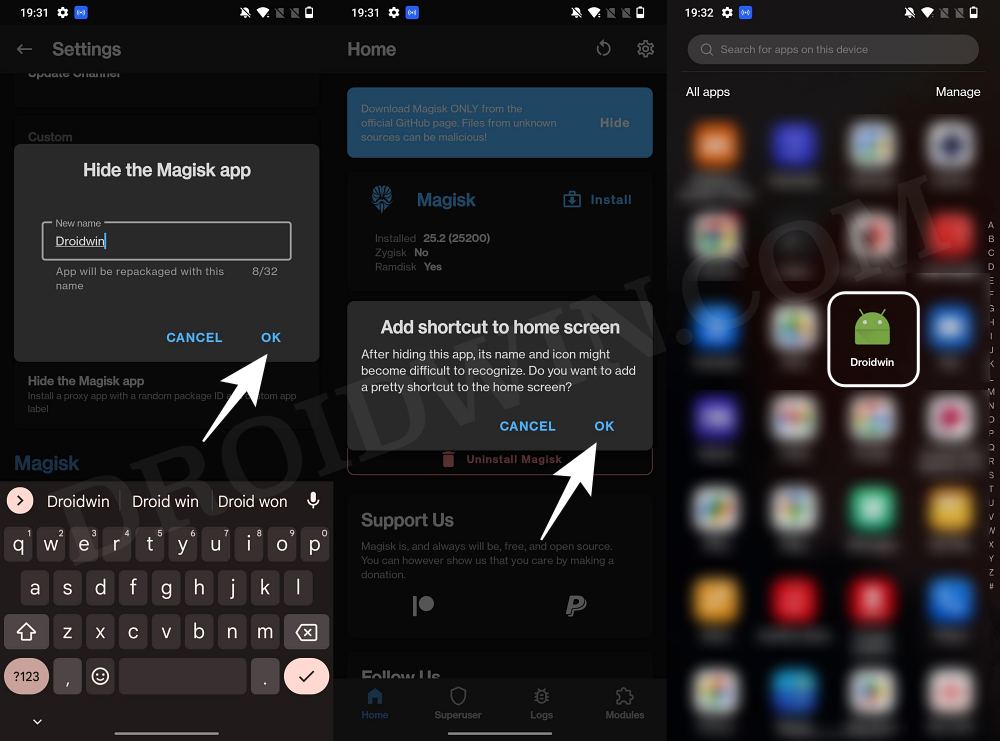
STEP 5: Hide the Magisk App on Nothing Phone 1
Some apps not only check for the SafetyNet flag but also verify if the Magisk app is installed onto your device or not. Therefore, let’s disguise this app so that it re-installs itself with a different package name. Follow along.
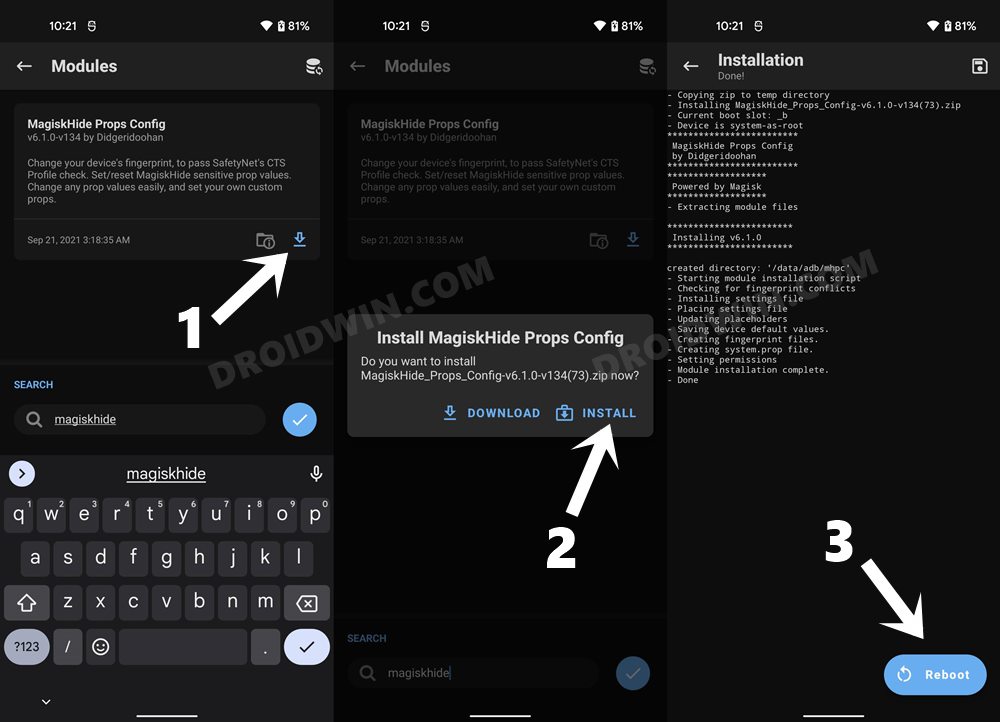
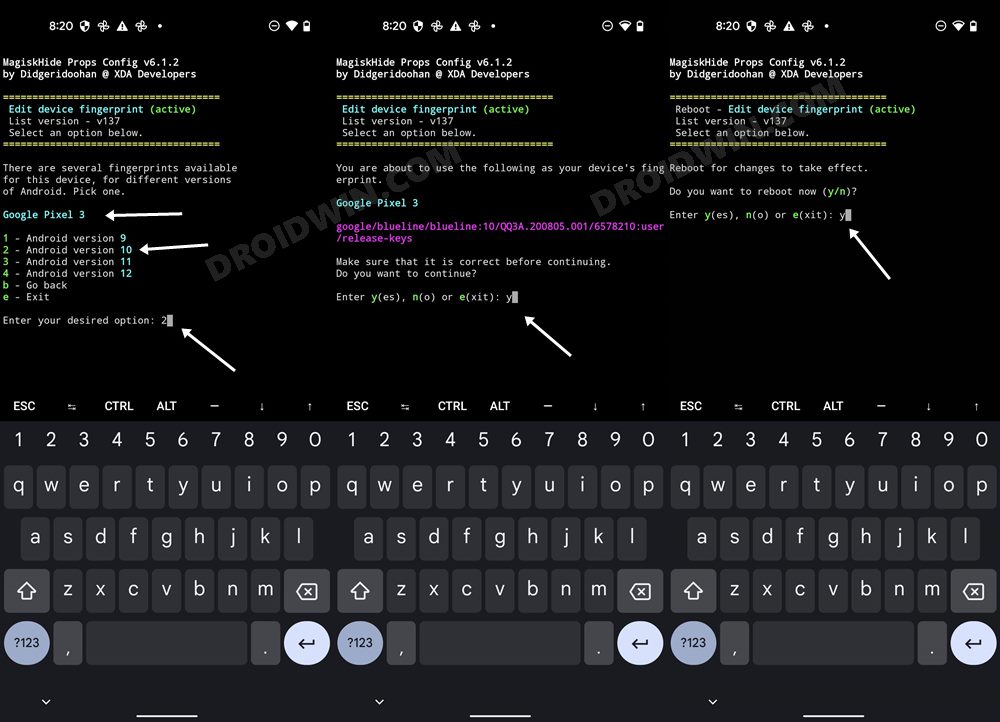
STEP 6: Install MagiskHide Props Config on Nothing Phone 1
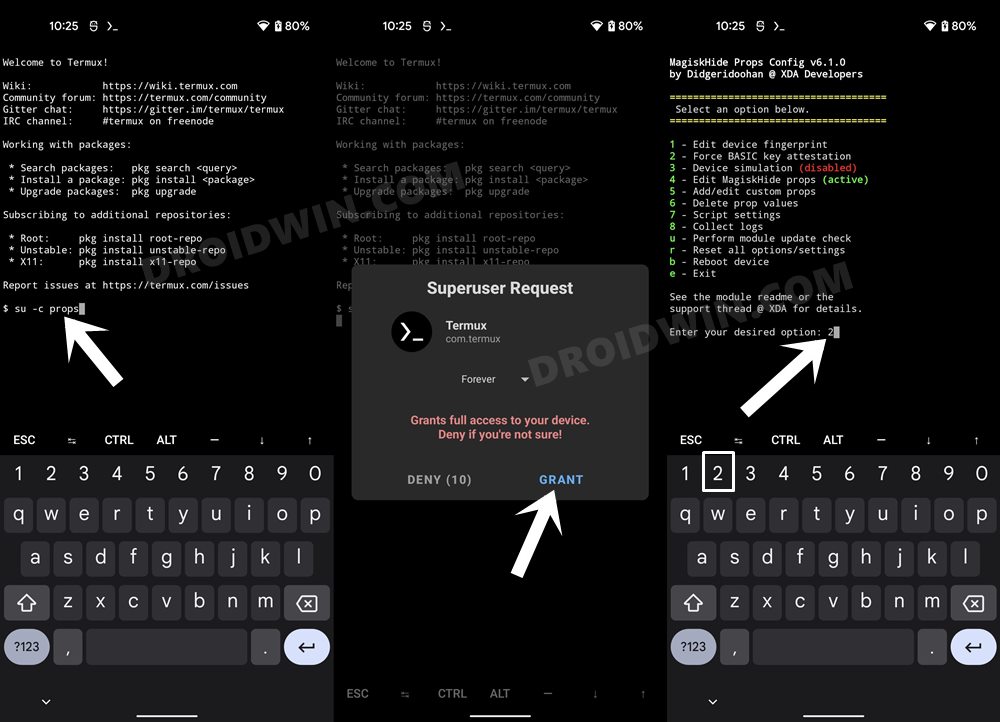
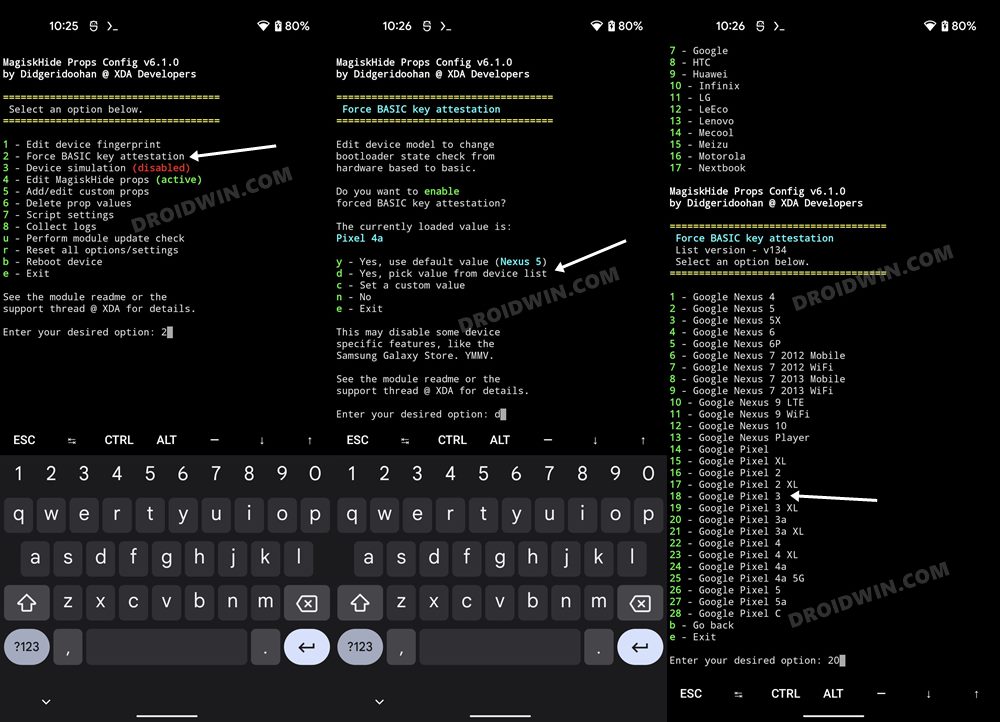
STEP 7: Force Basic Attestation on Nothing Phone 1
We will now be starting with the implementation of the BASIC attestation on top of the hardware-based so that it becomes easier to bypass. Here’s how it could be done:
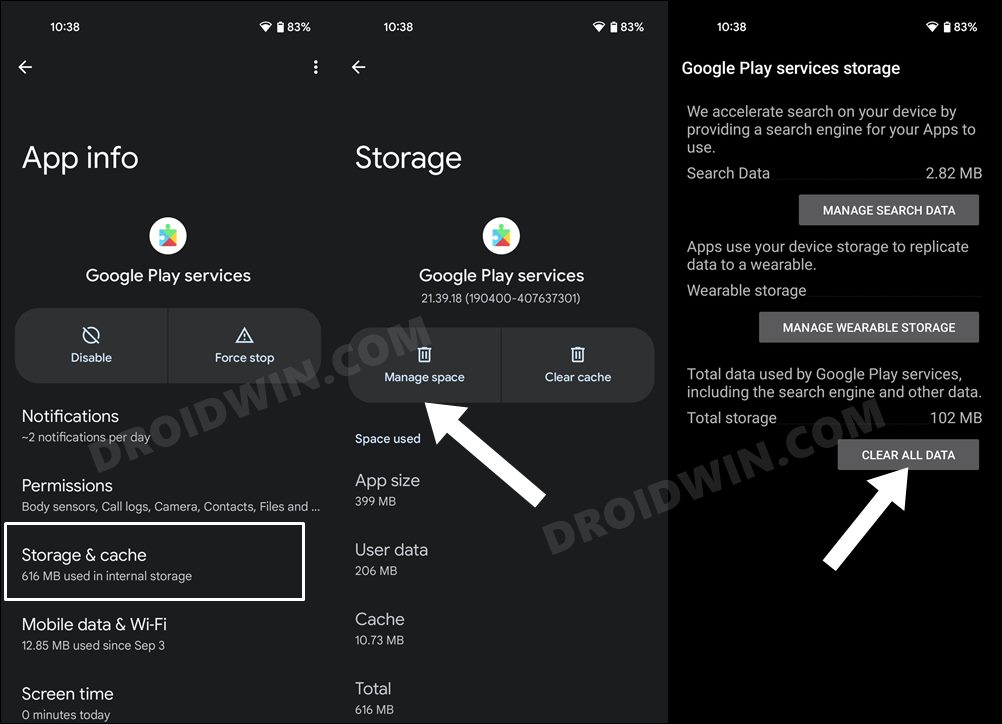
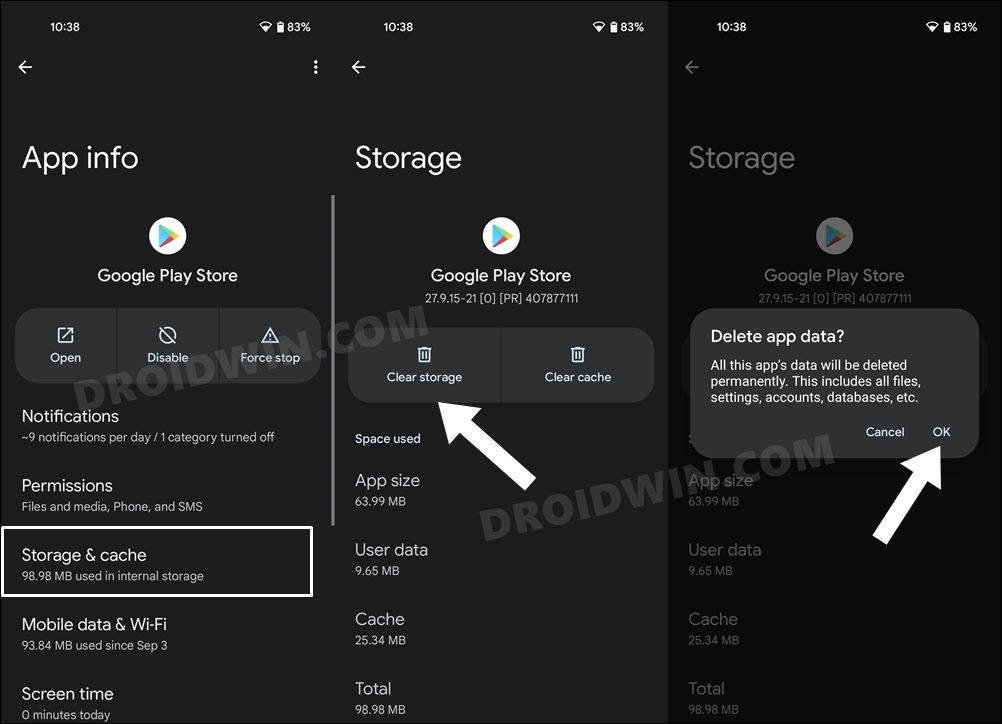
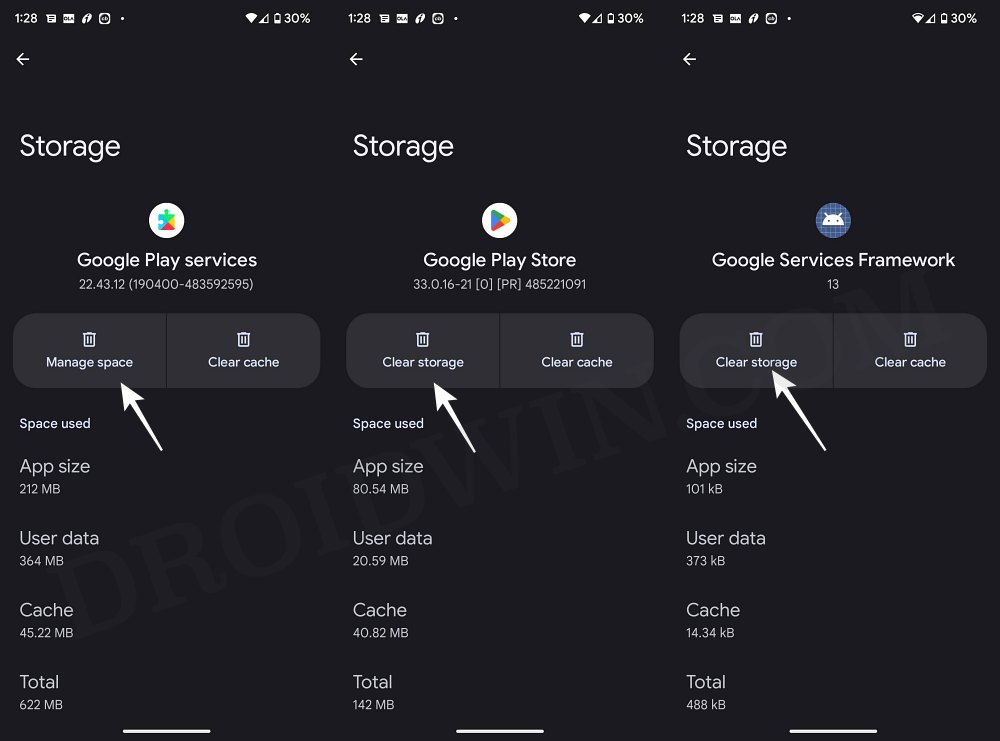
STEP 8: Delete Google Service Play Store Data
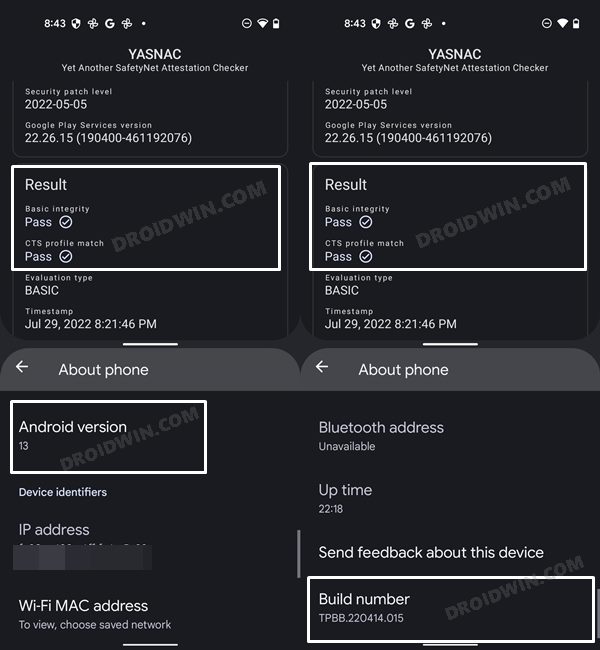
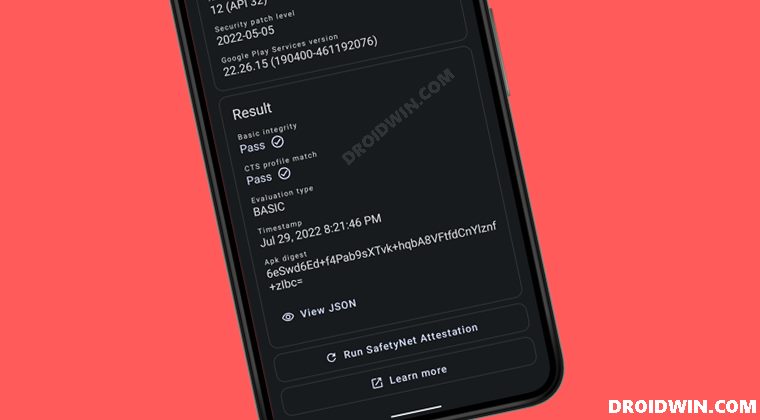
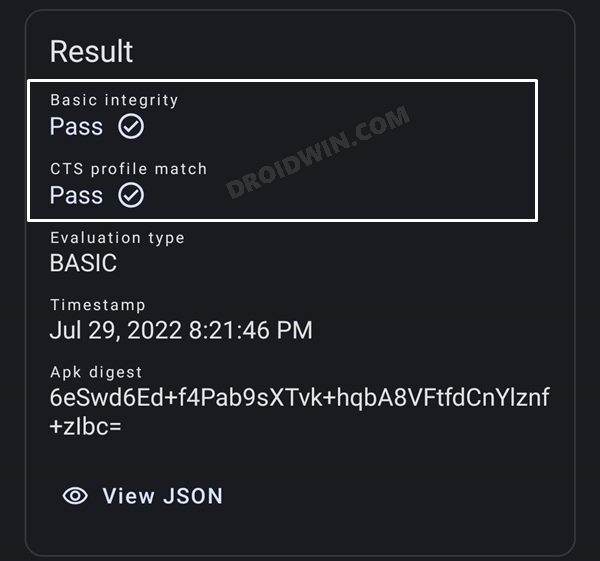
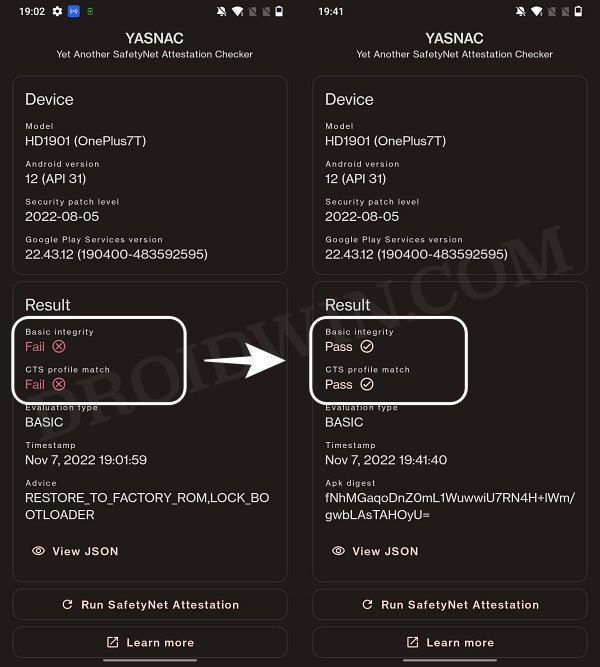
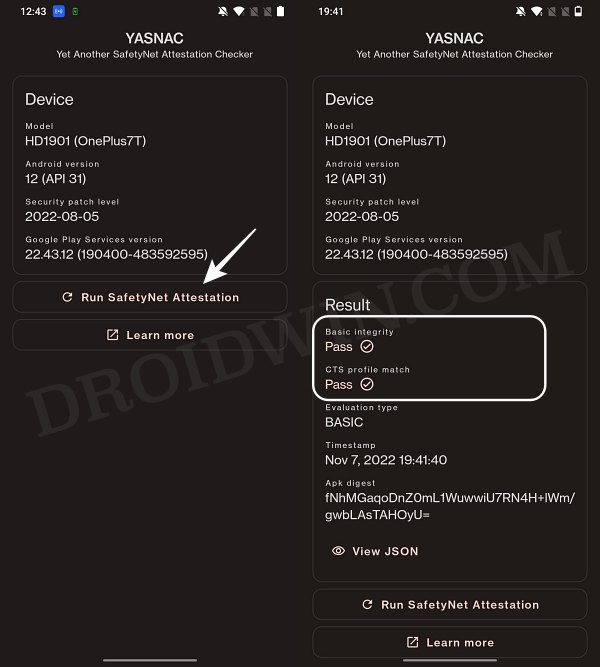
STEP 9: Check SafetyNet Result on Rooted Nothing Phone 1
So with this, you have successfully passed the SafetyNet on your rooted Nothing Phone 1. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
METHOD 2: Pass SafetyNet without Magisk Hide Props Config [NEW]
The shorter of the two methods, this doesn’t require you to spoof the device’s fingerprint or flash the Magisk Hide Props Config, all thanks to tweaks made by the developer of the Universal SafetyNet Fix Module. So on that note, let’s get started with the steps to pass Safetynet on your rooted Nothing Phone 1.
STEP 1: Hide Magisk App
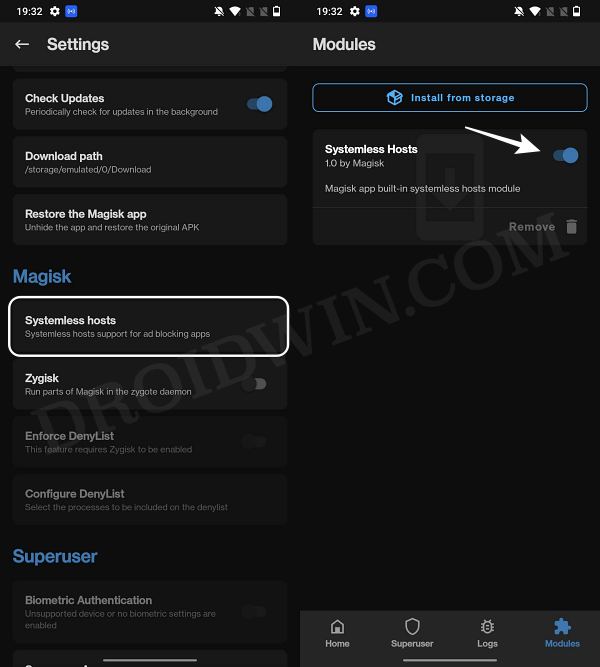
STEP 2: Enable Systemless Hosts
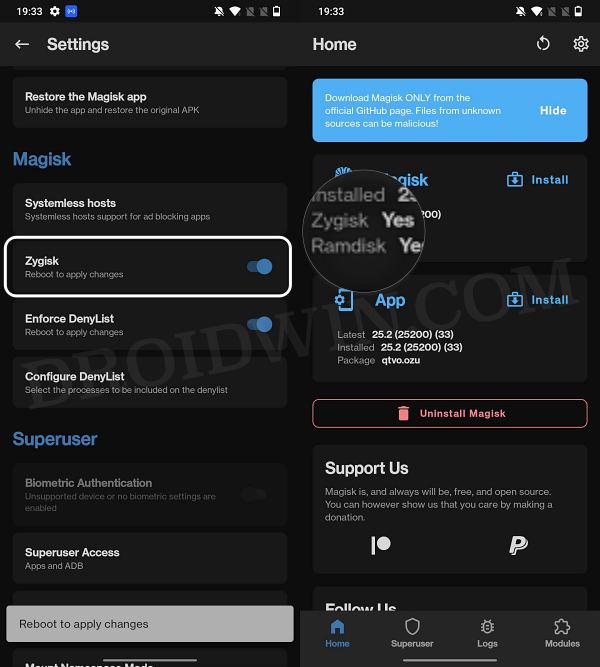
STEP 3: Enable Zygisk
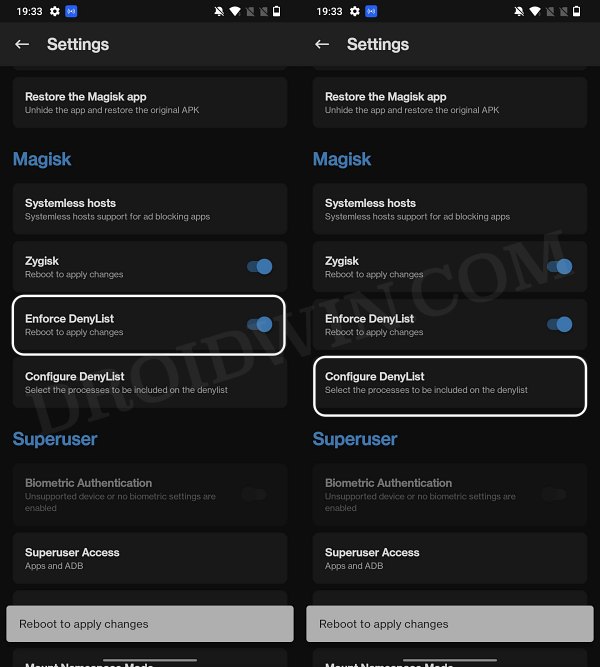
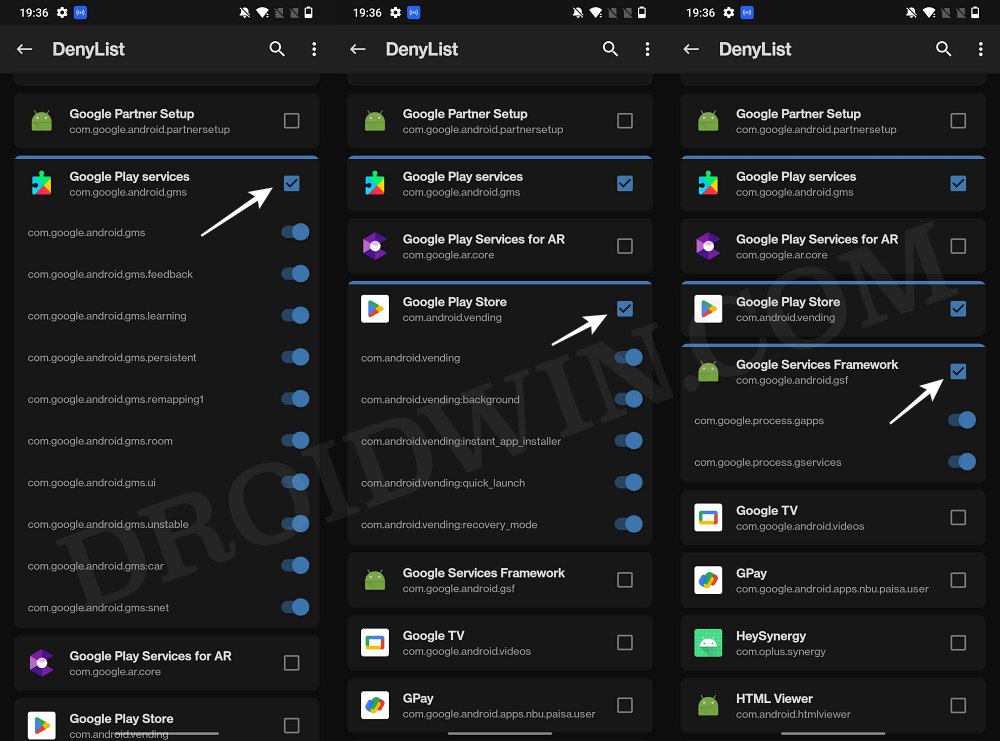
STEP 4: Configure Denylist
Denylist is the new name for the traditional Magisk hide. You could use this functionality to hide root from the desired apps, apart from the three compulsory apps listed below.
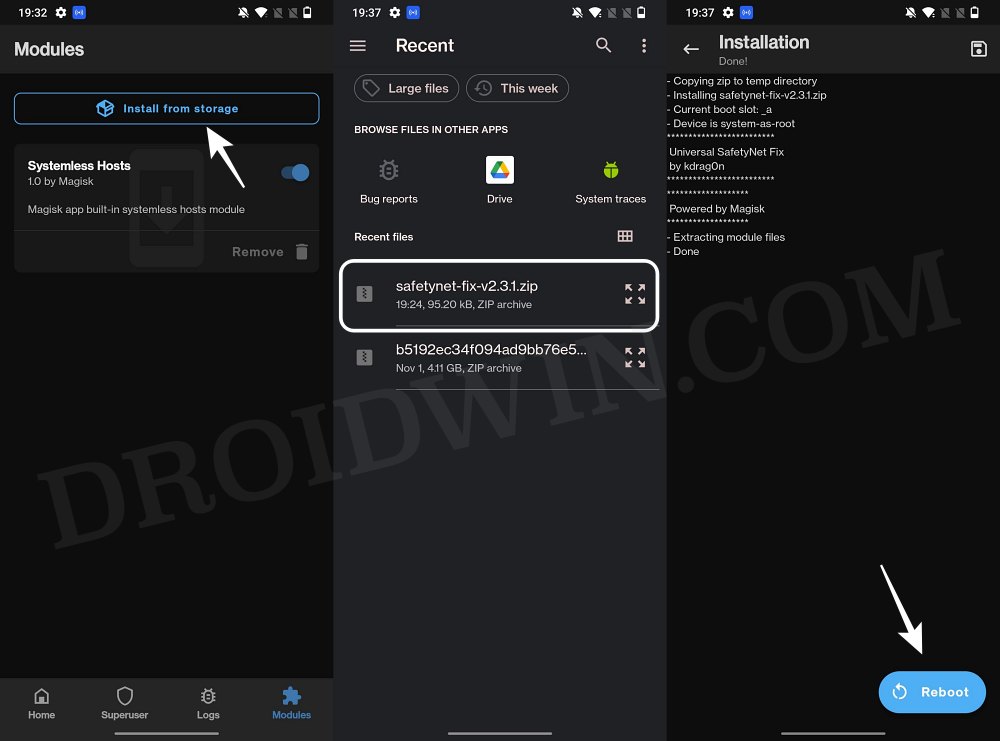
STEP 5: Flash Universal SafetyNet Fix Module
STEP 6: Delete Data
You will now have to delete the app data of all the apps from which you have hidden root. These include the compulsory Google apps and the desired apps of your choice.
STEP 7: Check SafetyNet Test Results
That’s it. these were the steps to pass SafetyNet on your rooted Nothing Phone 1. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
How to Pass SafetyNet test after installing Xposed or EdXposedFix Magisk Safetynet API Error: Detailed GuideHow to Fix ctsProfile Mismatch Error on Rooted AndroidBootloop after installing/updating Magisk: How to Fix
About Chief Editor