In this guide, we will show you how to pass the Magisk SafetyNet on your rooted Android 11 device. One of the biggest perks of having an open-source OS like Android is the fact that you could carry out a plethora of tweaks and customizations. The only requirement is that your device’s bootloader needs to be unlocked. Once that is done, you could install custom ROMs, flash custom recoveries like TWRP, Pixel Experience Recovery, etc. Along the same lines, you could gain administrative rights or access to the system partition. This is done by rooting the device via Magisk (with TWRP or without TWRP– by patching stock boot.img). Once you have achieved root, you could then flash tons on Magisk Modules, Xposed Framework, Substratum Themes, and plenty of other mods. However, these tweaks have some associated risks and caveats. When it comes to risk, if the steps aren’t performed correctly, then you could end up with a bootloop, soft-brick, or hard-bricked devices. In most instances, all these could easily rectified0 by flashing stock firmware via Fastboot or using the EDL mode in case of hard-brick. But all these are just one aspect. If we talk about the caveats or drawback, then there are quite a few. The most common issues result in the inability of various apps to function normally. For example, banking apps like Google Pay will just refuse to work. Likewise, games like Pokemon Go will not function on a rooted device. Talking about Netflix, its Widevine L1 certification degrades to L3, hence you wouldn’t be able to watch videos in HD. In all these cases, there was a simple workaround, just hide the device unlock and root status via Magisk. But now, with the latest Android version, things have become a little more complicated. However, there does still exists a nifty workaround through which you pass the Magisk SafetyNet on your rooted Android 11 device. And this tutorial will show you how this could be achieved. Follow along.
How to Fix ctsProfile Mismatch Error on Rooted AndroidHow to use Core Only Mode in the new Magisk Manager?Root Android 11 via Magisk Patched boot.img (without TWRP)Fix Magisk patched boot.img issue while Rooting Android 11
What is the Magisk SafetyNet Issue on Android 11?
I would try to keep this entire explanation as simple as possible, without incorporating any technical jargon. SafetyNet was introduced by Google to keep a check on device tampering. That is, if you have performed any system-level tweaks or installed any custom binary, then this SafetyNet will be trigged. it would then warn the installed apps to proceed ahead with caution. The reason for the same is that unlocking any device or rooting it breaks the security guarantee that the OEM has to offer. Your system partition is now easily accessible and hence could be accessed by unauthorized users. However, that usually doesn’t happen because the user who opts for these tweaks very well knows the risks associated with it and also how to fix any issue if he comes across. With that said, Google does its part and so do other apps. They simply check if SafetyNet has been tripped or not. If it has been, then the app will just refuse to function or work under limited capacity.
However, Magisk came with a pretty nifty method to bypass this restriction: you could easily hide root and unlock status from your device using a baked-in feature of Magisk. This way Safetynet wouldn’t be able to detect any modifications on your device and hence all the apps will function without any issues. But with the release of Android 11, things have taken a turn, and for worse! Up until now, SafetyNet only used two parameters to check if the device has any custom binaries installed or not. These were the ctsProfileMatch and basicIntegrity. However, there’s now a third parameter added to this list in the form of evaluationType.
Fix Magisk Module Bootloop without TWRP RecoveryHow to Fix TWRP Error 20 GApps after flashing LineageOSHow to Fix TWRP Error 70 [With Screenshots]Fix TWRP Error 7 (While Flashing Custom ROM via TWRP)
evaluationType: Basic vs Hardware
It is due to this third parameter, Magisk wouldn’t be able to hide the unlocked bootloader status from your device. On the other hand, the root hiding would still work along the expected lines. So the apps that verify if your device’s bootloader is unlocked or not, will no longer be able to work on a rooted device. But there does exist a handy workaround through which you could pass the Magisk SafetyNet on your rooted Android 11 device. This in turn will allow SafetyNet to return a False status- both for unlocked bootloader and root, although your device will be rooted and having an unlocked bootloader (well, obviously!). Follow along for the detailed instructions.
Does your device Support SafetyNet’s Hardware-based Attestation?
Before we list out the instruction steps, let’s make you aware of an important. There is a simple way of testing if your device supports the latest Hardware-based Attestation or not.
How to Pass Magisk Safety Net on Android 11 Root
Now that you are aware of the method to check for evaluationType/Hardware attestation, let’s check out the steps to pass the Magisk SafetyNet on your rooted Android 11 device. We have broken down the below steps into separate sections for ease of understanding. Follow along.
STEP 1: Enable MagiskHide
Fix error boot prepare- device stuck in fastbootFix Android stuck in Recovery Mode: No Command screenDetailed Steps to Fix adb is not recognized ErrorHow to Fix FAILED (remote: unknown command) Error
STEP 2: Randomizing Magisk Manager with another name
It’s now time to hide the Magisk Manager app from being identified by other apps. This in turn will be done by randomizing the app’s package name to any other name of your choice! As an example, I will be renaming it to Droidwin, so if any apps check for Magisk installation, they wouldn’t be able to find it since it has been masked under the DroidWin name. Sounds impressive, right? Well, it definitely is! Here’s what needs to be done in this regard:
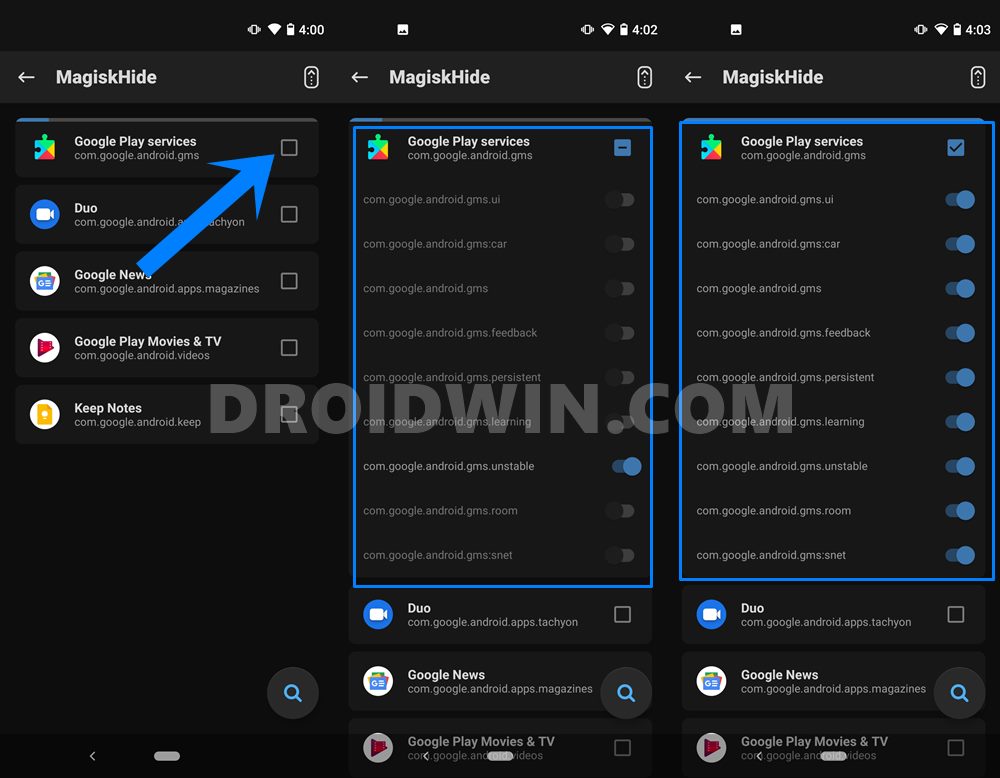
STEP 3: Hide Magisk SafetyNet from Google Apps, Services, and Frameworks
Just to be double sure, we would also be hiding the apps from the Google ecosystem. Here’s how:
Fix Magisk patched boot.img issue while Rooting Android 11Fix: pip is not recognized as an internal or external commandHow to Update Magisk ZIP and Magisk Manager (without TWRP)Fix Magisk Module Bootloop without TWRP Recovery
STEP 4: Spoofing your Device Fingerprints to Pixel 3A
Finally, it’s now time to change your device fingerprint identification and spoof it to Pixel 3A. But why? Well, this is because Pixel 3A was the last device in the Pixel series to use the old SafetyNet attestation method, which Magisk can hide from. So SafetyNet will hence perform its search using the old method itself and it wouldn’t be able to identify any system-level tweaks on your device. With the explanation now clear, here are the instructions to carry out this task:
STEP 5: Flash Universal SafetyNet Fix Magisk Module
So I went through all of your comments and it turns out that there are some users who aren’t able to pass the SafetyNet test on their rooted Android 11. It all seems to boil down to this hardware-backed attestation method. Here is what is actually happening with most users/ In order to verify and validate the CTS profile, Google Play Services is opting for the more stringent hardware-backed attestation even if you have selected the basic attestation. So it seems that Google is straightaway neglecting the report from the SafetyNet Attestation API that the device is using basic attestation and is rather directly going for the hardware-backed attestation. But thanks to XDA Senior Member kdrag0n he has managed to bypass this limitation as well, that too via a magisk Module. With that said, you still need to complete the first four steps mentioned above and then only should try out the instructions mentioned below.
So this was from this guide on how to fix the how to pass the Magisk SafetyNet on your rooted Android 11 device. If you have any queries, do let us know in the comments section below. We will get back to you with a solution at the earliest.
How to Extract OZIP Realme and Oppo Stock ROM (Firmware)How to Extract Stock Boot. img from OnePlus OxygenOS Stock ROM[GUIDE] Flash ROMs/Magisk/TWRP/Kernels on A/B Partition DevicesEverything About Magisk- Manager, Modules, and More
About Chief Editor












![]()

